Quick Summary: Identity and Access Management (IAM) is essential for safeguarding digital systems and ensuring that the right individuals have access to the right resources. From reducing security risks to enhancing operational efficiency, IAM plays a critical role in modern IT environments. It supports compliance with regulatory standards while enabling secure collaboration. This article breaks down its core capabilities, benefits, standards, and practical use cases.
Identity and Access Management (IAM) is a critical pillar of enterprise security in today’s interconnected digital environment. As organizations expand across cloud platforms, adopt hybrid work models, and navigate stringent compliance requirements, the need to manage user identities and control access to systems has become more urgent than ever.
In the absence of a unified IAM framework, businesses risk unauthorized access, privilege misuse, and potential data breaches, often stemming from simple oversights like orphaned accounts or over-permissioned users. These gaps not only compromise data integrity but can also lead to operational disruptions and regulatory penalties.
The system helps organizations overcome access-related risks by verifying users, applying policy-driven permissions, and continuously tracking system activity. In this blog, we’ll delve into the fundamentals of IAM, explore its key components, and understand how it strengthens security while enabling efficiency at scale.
What is Identity and Access Management (IAM)?

Identity and Access Management (IAM) is a centralized framework that governs how digital identities are created, authenticated, and authorized within an organization’s IT environment. It involves defining user identities and mapping them to roles or policies that specify the resources they can access and the actions they are allowed to perform, such as viewing files, submitting requests, or administering systems.
IAM systems operate through access control mechanisms like role-based or attribute-based policies, applied consistently across on-premises and cloud platforms. These systems not only manage who can access which applications or data but also ensure that permissions stay aligned with business roles, compliance mandates, and lifecycle events.
Four Core Control Functions of Identity and Access Management (IAM)
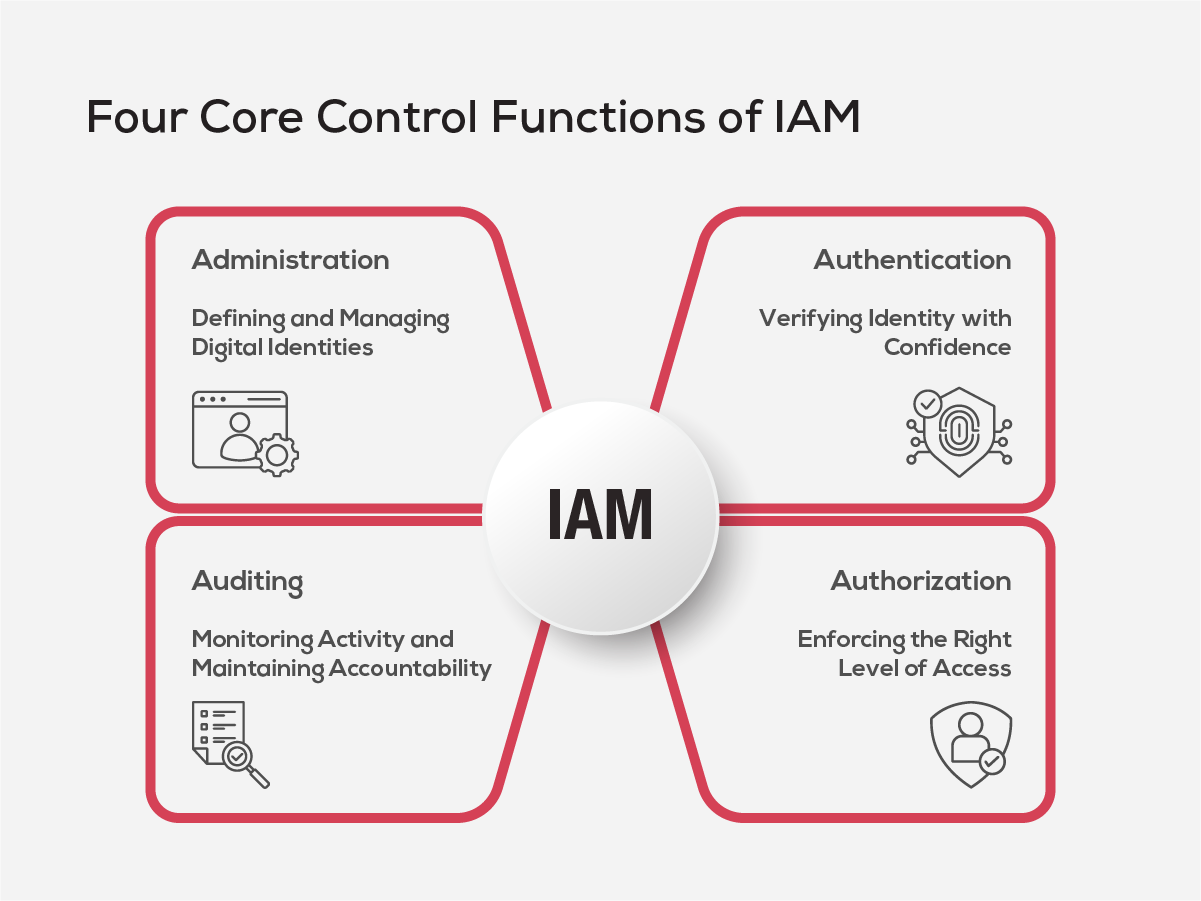
Every effective IAM strategy has four core control functions that ensure identities are managed securely, access is granted appropriately, and oversight is maintained at every stage. These form the operational foundation that enables secure, efficient, and compliant identity management across enterprise systems.
1. Administration: Defining and Managing Digital Identities
Administration governs the lifecycle of every identity within the system. This includes creating new user accounts, assigning roles, updating access as responsibilities evolve, and securely deactivating accounts when users exit the organization. Each identity is associated with key attributes, such as department, job role, or location, that determine what level of access the user should have.
Centralized identity repositories serve as the source of truth, helping IAM solutions maintain consistency and avoid conflicts. Automation can streamline onboarding and role-based provisioning reducing manual errors and accelerating access delivery while maintaining control.
2. Authentication: Verifying Identity with Confidence
Authentication ensures that access requests come from legitimate users, not imposters. It does so by requiring one or more identity authentication factors, such as passwords, smart cards, biometrics, or one-time passcodes. The goal is to validate user claims securely before access is even considered.
To strengthen assurance, most modern IAM systems adopt multi-factor authentication (MFA), which significantly raises the security threshold by combining independent verification methods, protecting against credential theft and unauthorized access.
3. Authorization: Enforcing the Right Level of Access
Authorization takes over once identity has been confirmed. It determines what actions a verified user can perform and which resources they can interact with. IAM systems apply policies that align with organizational structures, using models like Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC).
These access rules are shaped by the principle of least privilege, ensuring that users only receive the minimum permissions required to perform their tasks—no more, no less. This prevents overexposure and limits the potential impact of both human error and malicious activity.
4. Auditing: Monitoring Activity and Maintaining Accountability
Auditing introduces visibility and accountability into the IAM framework. It involves capturing logs of access events, tracking changes to identities and permissions, and generating reports to support internal oversight or external regulatory audits.
This function is vital not only for compliance with standards like GDPR, SOX, and PCI DSS, but also for detecting suspicious behaviour, identifying policy violations, and continuously refining identity governance practices. A strong auditing capability ensures that every action taken within the system can be traced, verified, and justified.
Without these core controls, identity management would lack the structure, consistency, and accountability that today’s digital environments demand.
IAM Security Capabilities That Strengthen Digital Trust

The current digital landscape demands more than just user verification, it calls for layered security measures that adapt to risk, streamline access, and protect sensitive systems without friction. IAM solutions bring together a suite of specialized capabilities designed to meet these needs, each playing a critical role in reinforcing identity integrity and ensuring trusted access across the enterprise.
1. Single Sign-On (SSO)
Single Sign-On simplifies the login process by enabling users to access multiple applications or systems using one set of credentials. Rather than remembering different usernames and passwords, users authenticate once and gain seamless access to integrated services. This not only improves convenience and productivity but also reduces password fatigue and the likelihood of password-related vulnerabilities. SSO is typically backed by a trusted identity provider that verifies user credentials and manages access across platforms.
2. Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) strengthens identity verification by requiring two or more distinct factors such as something the user knows (e.g., a password), something they possess (e.g., a mobile code or security token), or something inherent to them (e.g., fingerprint or facial features). This layered approach greatly lowers the chances of unauthorized access resulting from compromised or stolen credentials.
3. Privileged Access Management (PAM)
Privileged accounts, those with administrative or elevated access, are prime targets for attackers. PAM solutions help manage, monitor, and secure these accounts by enforcing strict controls on who can access sensitive systems and how those permissions are granted. Features like session recording, time-bound access, and approval workflows help minimize insider threats and prevent misuse of high-level privileges.
4. Risk-Based Authentication (RBA)
RBA dynamically evaluates the risk of each login attempt based on contextual factors such as location, device type, IP reputation, and user behaviour. When an access request is flagged as unusual or high-risk, the system can enforce additional authentication steps or block the attempt altogether. This adaptive approach balances user convenience with proactive threat mitigation.
5. Data Governance
Data governance within IAM focuses on ensuring the integrity, security, and ethical use of identity-related data. As IAM solutions increasingly integrate AI and ML for decision-making, the quality and consistency of underlying data become critical. Policies around data handling, classification, and access controls help ensure that identity data is accurate, up to date, and protected from misuse.
6. Federated Identity Management
Federated identity allows users to access services across multiple organizations using a single digital identity. Through trust agreements and shared authentication protocols, users can seamlessly move between systems, such as those of partners, vendors, or external platforms, without needing to create new accounts. This not only improves the user experience but also reduces the burden of managing separate credentials.
7. Zero Trust Access
Zero Trust is a security philosophy that assumes no user or device is inherently trustworthy, even if inside the network perimeter. IAM plays a pivotal role in Zero Trust by continuously verifying user identity, enforcing granular access controls, and monitoring activity in real time. By treating every access attempt as potentially risky, Zero Trust helps organizations prevent lateral movement and reduce exposure to threats.
8. Identity Governance and Administration (IGA)
IGA combines visibility, policy enforcement, and automation to manage identities across their lifecycle. It ensures users have appropriate access aligned with their roles while enforcing compliance with internal policies and regulatory standards. IGA capabilities include role management, access certification, automated provisioning, and reporting, ensuring that access is consistently monitored, reviewed, and adjusted as needed.
As identity becomes the new perimeter, these capabilities help enterprises stay ahead, enabling secure access, mitigating risks, and empowering users with confidence.
Top Benefits of Identity and Access Management (IAM)
Implementing IAM brings measurable advantages across security, efficiency, and user experience. From safeguarding critical data to streamlining operations, the benefits of IAM help organizations stay secure, agile, and compliant in a digital-first environment.
1. Reduced Administrative Overhead
IAM automates the process of managing user identities, roles, and access permissions, which significantly eases the administrative burden on IT teams. Routine tasks like onboarding, role changes, and deprovisioning are simplified through centralized policies and automated workflows. This not only improves operational agility but also ensures that access rights are consistently applied across the organization.
2. Strengthened Security Posture
With IAM, organizations can tightly control who has access to what, reducing the attack surface and minimizing the risk of internal misuse or external breaches. Capabilities like multi-factor authentication (MFA), session controls, and behavioural analytics ensure only authorized users access sensitive systems. IAM also supports dynamic policy enforcement based on user context, making it harder for threat actors to exploit credentials.
3. Lower Operational and Security Costs
Though the initial setup may involve investment, IAM ultimately reduces long-term costs by consolidating access management tools, preventing security incidents, and ensuring smoother audits and compliance checks. By minimizing the risk of regulatory violations and data breaches, IAM helps organizations avoid legal penalties, reputational damage, and costly remediation efforts.
4. Centralized and Consistent Security Enforcement
A unified approach to access policy enforcement ensures that security rules remain consistent across both on-premises and cloud systems. With a single source of identity truth, organizations can confidently apply uniform controls, strengthen compliance and support key frameworks like the principle of least privilege.
5. Simpler and Error-Free User Management
With role-based and attribute-based access controls, IAM ensures that users only receive the permissions necessary for their job functions. Automated provisioning reduces manual intervention, lowering the risk of misconfigured access and human error. Whether it’s a new hire or an internal role shift, changes are reflected promptly and securely across systems.
6. Proactive Access Monitoring and Control
IAM provides audit trails and logging mechanisms to track how users interact with systems and data. This visibility helps security teams detect anomalies, investigate incidents, and maintain regulatory compliance. Continuous monitoring ensures that access remains appropriate as roles evolve and helps prevent unauthorized activity before it escalates into a threat.
7. Secure and Seamless Collaboration
The ability to grant secure access to employees, partners, and third-party vendors without compromising data integrity is a strategic advantage. Shared resources can be accessed based on defined roles or policies, enabling safe collaboration across departments and geographies. IAM ensures that sensitive information is only available to the right individuals, fostering both productivity and accountability.
These advantages demonstrate that IAM simplifies secure access, helping people work smarter while keeping systems protected.
IAM Integration Standards
Modern IAM systems rely on a foundation of technical standards to stay compatible with the growing number of cloud services, applications, and user environments. These standards ensure secure data exchange, consistent user access, and smooth integration across systems.
OAuth 2.0: Secure Delegated Access
OAuth 2.0 is a widely used authorization framework that allows applications to access user resources without sharing login credentials. Instead of passwords, it uses access tokens to enable permission-based access to APIs across web, mobile, and IoT environments. By separating authentication from authorization, OAuth 2.0 supports secure integration for services like Google, Facebook, and other major platforms.
OpenID Connect (OIDC): Lightweight, Modern Authentication
Built on top of OAuth 2.0, OpenID Connect is a modern identity protocol that uses RESTful APIs and JSON payloads for secure user authentication. Unlike SAML, which is XML-based, OIDC is designed to work efficiently with native and mobile applications. It is often the preferred choice for developers seeking lightweight, scalable SSO implementations in cloud-first architectures.
SAML: Federated Authentication for Enterprises
Security Assertion Markup Language (SAML) enables identity providers to securely transmit authentication and authorization data to service providers. Commonly used in enterprise environments, SAML supports Single Sign-On (SSO) for web applications by using XML to facilitate identity exchange. It is a key standard for enabling trusted access across organizational boundaries.
SCIM: Simplified User Provisioning
The System for Cross-Domain Identity Management (SCIM) standard is designed to streamline identity management across cloud-based applications. It automates the process of provisioning, updating, or deactivating user accounts, reducing administrative overhead and ensuring consistency across platforms. SCIM enhances operational efficiency and helps enforce access policies in dynamic cloud ecosystems.
LDAP: Directory-Based Identity Access
The Lightweight Directory Access Protocol (LDAP) is a longstanding standard used to store, retrieve, and authenticate user data in centralized directories. It plays a critical role in user access verification and supports features like Single Sign-On, role-based access control, and encrypted communications through SSL or TLS. LDAP remains essential in many enterprise IT environments, particularly for legacy application support.
Regulatory Alignment through IAM
Identity and Access Management plays a pivotal role in helping organizations meet cybersecurity requirements outlined by industry regulations and security frameworks. Whether the goal is to protect personal data, manage system access, or maintain audit trails, IAM serves as a foundational element for regulatory alignment across sectors.
Here are some notable regulations where IAM capabilities are either explicitly required or strongly recommended:
- FISMA (Federal Information Security Management Act):
Mandates federal agencies and contractors to implement security controls, including identity-based access restrictions, to safeguard government systems and data.
- GDPR (General Data Protection Regulation):
Emphasizes strict access controls and user consent management to ensure the confidentiality and integrity of personal data processed within the EU and beyond.
- HIPAA (Health Insurance Portability and Accountability Act):
Requires healthcare organizations to restrict access to Protected Health Information (PHI) based on user roles, supported by authentication and audit mechanisms.
- ISO/IEC 27001:
An international standard for information security management, which includes controls around access provisioning, user identity verification and privilege management.
- PCI DSS (Payment Card Industry Data Security Standard):
It requires businesses that handle payment data to implement strict access controls and multifactor authentication on any systems storing sensitive cardholder information.
- SOX (Sarbanes-Oxley Act):
Focuses on internal controls over financial reporting, which includes secure user authentication and access control to critical systems handling financial data.
- NIST Cybersecurity Framework (CSF):
Offers structured guidance for managing cybersecurity risks, highlighting identity management as a key function within access control and protective technologies.
Conclusion
In today’s volatile threat landscape, identity is the new perimeter and it’s constantly under attack. With users spread across cloud, mobile, and hybrid environments, the margin for error has narrowed. IAM is no longer optional, it is foundational. Therefore, without it, organizations risk unauthorized access, compliance violations, operational downtime, and irreversible brand damage.
This makes a well-governed IAM strategy the need of the hour, not just for large enterprises, but for every business that interacts digitally. It ensures that the right people have the right access, for the right reasons, at all times.
Inspirisys brings this control to the forefront with its Identity and Access Management services. From access governance and policy enforcement to federated identity management and role-based controls, our IDAM services are designed to adapt to your ecosystem, scale with your growth, and secure your users, wherever they are.
We don’t just manage identities—we enable smarter, safer access at every layer of your digital infrastructure.
Frequently Asked Questions
1. Why is Identity and Access Management (IAM) important?
IAM helps organizations secure digital identities and control access to systems, applications, and data. It reduces security risks, ensures compliance with regulations, supports secure remote access, and improves operational efficiency by automating user access processes.
2. What’s the difference between identity management and access management?
Identity management is about creating, verifying, and managing digital user identities. Access management, on the other hand, determines what those verified users can do—what systems, applications, or data they can access—based on their roles and permissions. Together, they ensure that the right people have the right access at the right time.
3. What is privileged access management (PAM)?
Privileged Access Management (PAM) is the process of controlling and monitoring accounts that have elevated permissions, like admin accounts. PAM solutions help limit what high-level users can access or do, track their activities, and prevent misuse. This helps reduce risks from insider threats, data breaches, or unauthorized actions.
4. What is a directory service?
A directory service is a centralized system used to store and manage identity-related information such as usernames, passwords, devices, and access rights. It plays a key role in user authentication and authorization across networks. Common examples include Microsoft Active Directory, LDAP, and Azure Active Directory.







