Quick Summary: Web application penetration testing plays a pivotal role in identifying security flaws before they can be exploited. This guide delves into various testing methodologies, essential tools, and advanced techniques to fortify web applications. It also examines legal and ethical guidelines, common pitfalls, and best practices for establishing a resilient security framework. Continuous testing is key to proactively defending against ever-evolving cyber threats.
What is Web Application Penetration Testing?
Web application penetration testing is a critical security practice designed to proactively uncover and address vulnerabilities within web applications. As part of Vulnerability Assessment and Penetration Testing (VAPT), this approach combines automated vulnerability scanning with simulated real-world cyberattacks to evaluate an application’s resilience against unauthorized access, data breaches and other malicious threats. By identifying and rectifying security flaws—ranging from simple code errors to complex loopholes—web application penetration testing ensures that protective measures are both effective and well-structured. This proactive web security strategy safeguards sensitive data, supports regulatory compliance, and builds digital trust by mitigating risks before they can be exploited, making it a cornerstone of modern cybersecurity practices.
Why is Penetration Testing Important?
Industries such as e-commerce, online banking, healthcare, ERP, CMS, and financial management platforms rely heavily on web applications to handle sensitive data. Securing these applications throughout the software development lifecycle is critical, especially for those accessible online, as they are frequent targets for cyber threats.
To mitigate risks and prevent security breaches, penetration testing plays a key role in identifying vulnerabilities before they can be exploited. Here’s why regular penetration testing is essential for maintaining a strong security posture.
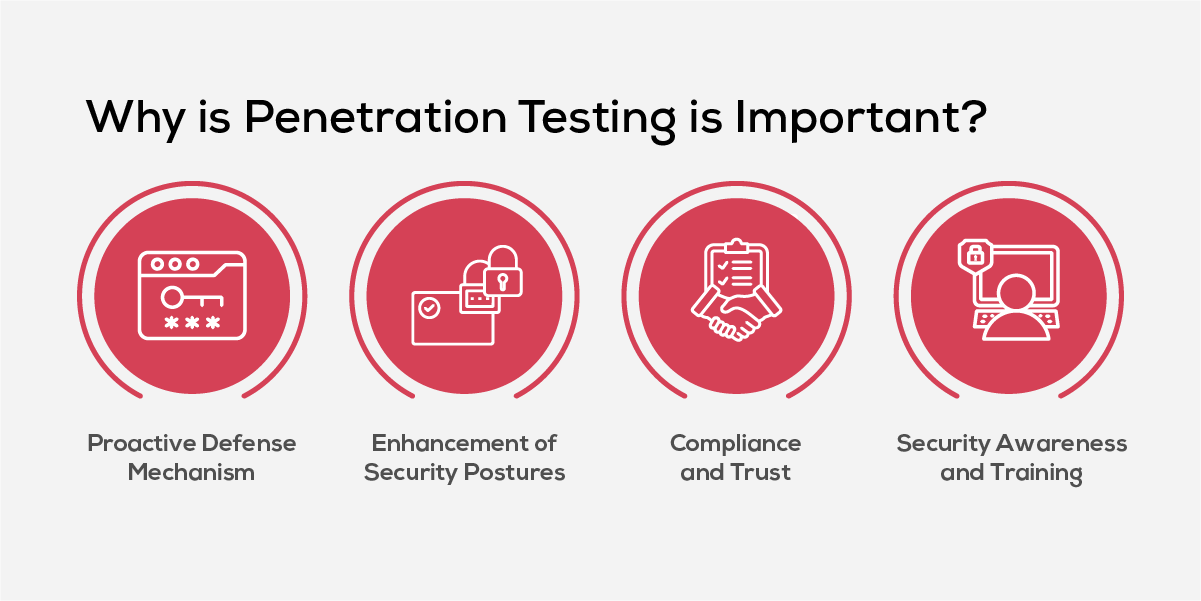
- Proactive Defense Mechanism: Penetration testing serves as an early warning system, simulating real-world cyberattacks to uncover weaknesses in systems, networks, and web applications. By detecting these gaps in advance, security teams can take action to prevent unauthorized access and reduce the likelihood of data breaches.
- Enhancement of Security Posture: Through continuous evaluation, organizations can measure the effectiveness of their current security controls and make informed improvements. This ongoing refinement ensures a more resilient cybersecurity framework capable of adapting to new and emerging threats.
- Compliance and Digital Trust: Regular penetration testing supports compliance with international cybersecurity standards and regulatory frameworks such as GDPR, PCI DSS, and ISO 27001. It helps avoid legal penalties while reinforcing digital trust among customers, partners, and stakeholders.
- Security Awareness and Workforce Training: Penetration testing also plays a crucial role in security training and awareness. It helps identify potential security gaps and educates the organization's workforce about the practical implications of cyber threats, reinforcing the importance of vigilance in everyday operations.
When implemented consistently, penetration testing helps strengthen digital defenses, ensure business continuity, and build a security-conscious organization.
Web Application Penetration Testing Process
Web application penetration testing follows a structured approach to identify, analyze, and validate security vulnerabilities. Each phase plays a critical role in measuring an application’s resilience to real-world threats. Here’s a step-by-step breakdown of how penetration testing is typically carried out for web applications.
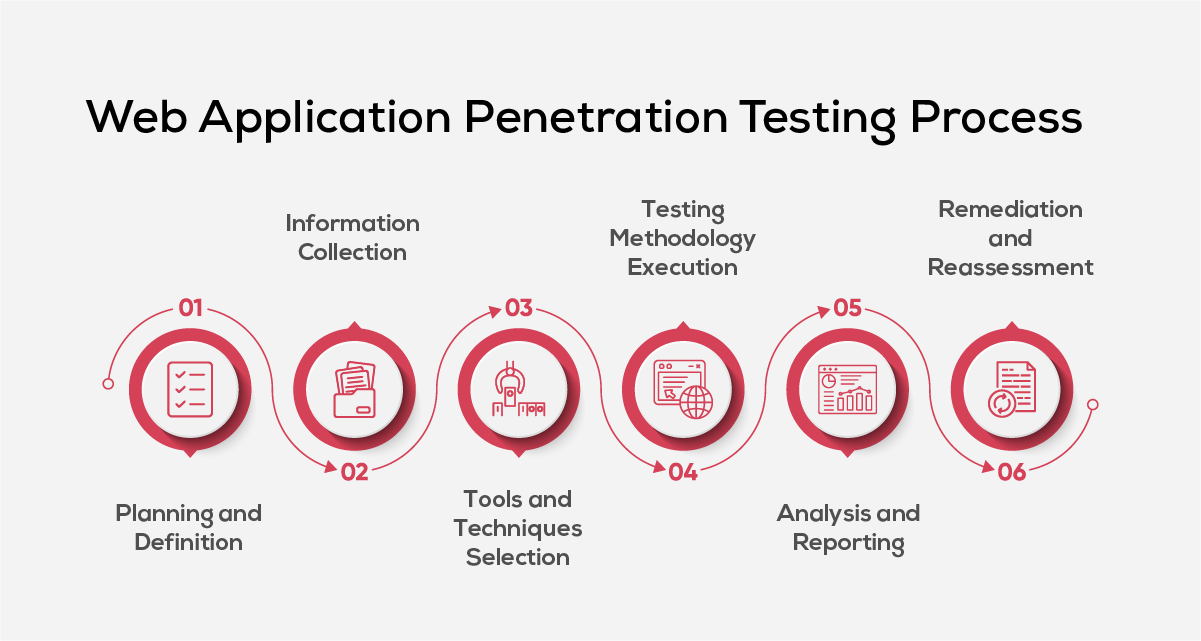
Step 1: Planning and Definition
Initiate your web application penetration testing with thorough planning. Determine which components of your application need testing—be it APIs, modules or entire systems. Decide whether to conduct internal tests or hire external security testing experts and establish clear objectives for the testing process. This initial clarity will streamline the overall vulnerability assessment effort.
Step 2: Information Collection
This step involves deep reconnaissance of your application. Collect detailed information about the app’s architecture, programming languages used, server configurations, and third-party integrations. This information gathering phase lays the groundwork for effective testing.
Step 3: Tools and Techniques Selection
Select appropriate penetration testing tools for your assessment. Combining automated vulnerability scanners with manual testing can provide comprehensive coverage. Automated tools can quickly detect common web application vulnerabilities, while manual methods allow for in-depth exploration of complex security issues.
Step 4: Testing Methodology Execution
Execute the penetration test using a methodology aligned with your security goals:
- Black-Box Testing: Simulates external attacks without prior internal knowledge.
- White-Box Testing: Provides testers with complete information, including source code, for a thorough assessment.
- Gray-Box Testing: Offers a mix of both, with limited access to some internal details.
Step 5: Analysis and Reporting
After testing, analyze the findings to assess and categorize identified vulnerabilities. Prioritize them based on severity and potential business impact. Deliver a penetration testing report that includes actionable remediation steps and is clear to both technical and business teams.
Step 6: Remediation and Reassessment
Finally, remediate identified web application vulnerabilities through patching, secure code updates, or configuration changes. After implementing fixes, conduct a retest to verify resolution and reinforce your web application’s overall security posture.
Types of Web Application Penetration Testing
Exploring different types of web application penetration testing is essential for building a comprehensive web application security strategy. Each testing method focuses on distinct areas of vulnerability, offering a layered approach to identifying and mitigating potential security threats.
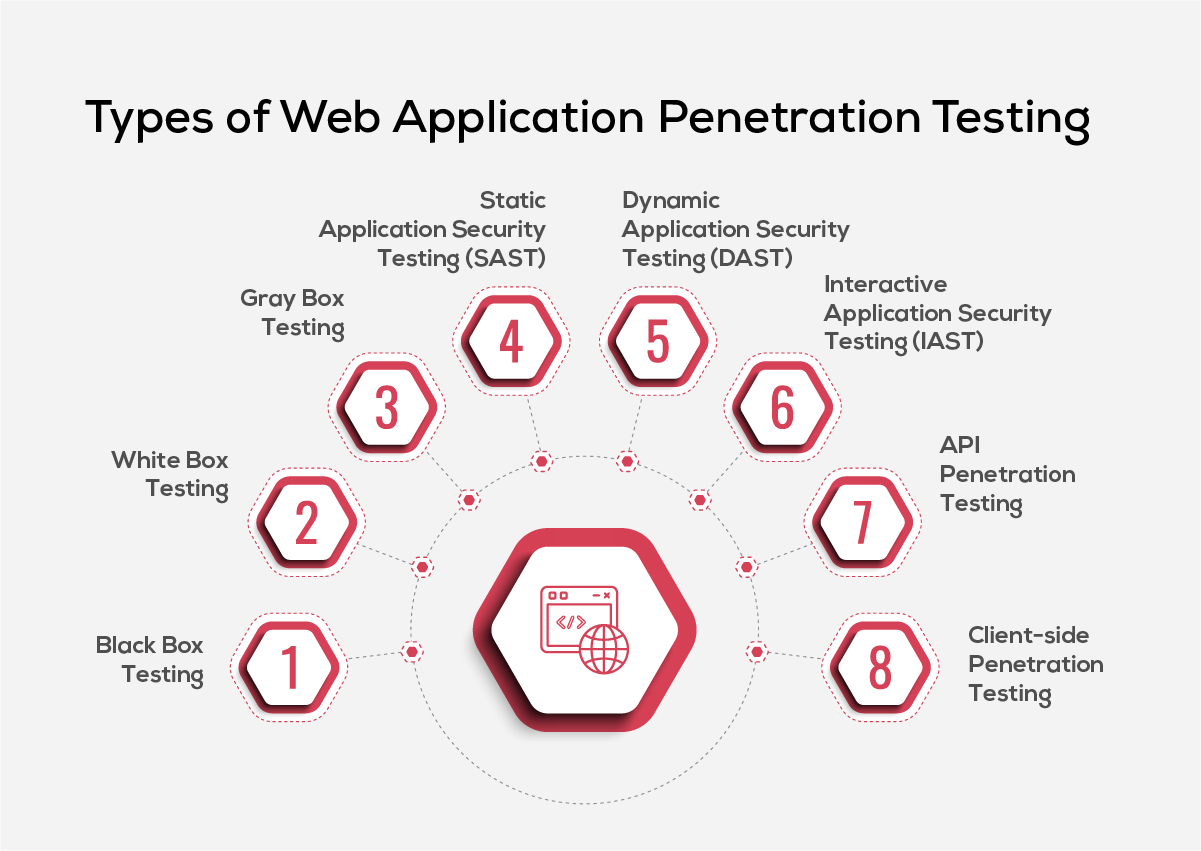
- Black Box Testing: This method approaches web applications as a mystery or unknown entity, where testers simulate external attacks without any prior knowledge of the system's internals. By mimicking real-world attacks, black box testing evaluates the robustness of an application's external defenses, identifying web application vulnerabilities that are exposed to anyone without inside access.
- White Box Testing (Clear Box/Glass Box Testing): Offering complete transparency, white box testing provides testers with full disclosure of the application’s environment, including source code, architecture, and credentials. This comprehensive visibility allows for an in-depth security assessment of the application’s logic, structure, and potential internal vulnerabilities, making it a powerful approach for identifying hidden security weaknesses.
- Gray Box Testing: Combining elements of both black and white box testing, gray box testers have partial knowledge of the application's internals. This approach provides a balance between in-depth, targeted testing and the unpredictability of external attacks, giving testers a nuanced perspective that is less informed than white box testing but more insightful than black box testing.
- Static Application Security Testing (SAST): SAST tools analyze an application's source code, bytecode, or binaries without executing the program. This static analysis scrutinizes the codebase for potential security issues, allowing teams to identify vulnerabilities early in the development lifecycle, often during the coding phase, which helps mitigate risks before deployment.
- Dynamic Application Security Testing (DAST): Contrary to SAST, DAST tests the application in its running state, actively probing for vulnerabilities that manifest during operation. This technique is especially effective for uncovering runtime issues such as those in session management and authentication that are not visible in static code analysis.
- Interactive Application Security Testing (IAST): IAST tools monitor the application from within as it runs, combining the benefits of SAST and DAST. By analyzing the application in real-time, IAST detects complex vulnerabilities and understands how data moves through the application, providing a detailed assessment of security issues.
- API Penetration Testing: With APIs being integral to modern web applications, API security testing focuses on the specific security aspects of these interfaces. This testing scrutinizes how APIs handle data, manage authentication, and interact with other app components, ensuring that the APIs uphold strong security standards and are resistant to exploitation.
- Client-side Penetration Testing: This type of testing targets vulnerabilities in client-side technologies like HTML, JavaScript, and CSS. It identifies security flaws that attackers could exploit through a user’s browser, such as cross-site scripting (XSS) and cross-site request forgery (CSRF), which can compromise user interactions and sensitive data.
Understanding the spectrum of web application penetration testing types equips security teams with the knowledge to tailor their testing strategies effectively. By selecting the right methods for your specific environment, you can enhance your security posture, reduce risks more efficiently, and ensure comprehensive protection against a wide range of cyber threats.
Common Pitfalls in Penetration Testing
Avoiding common pitfalls in web application penetration testing is important because each oversight can lead to significant security risks. Here is how each mistake can lead to a potential consequence:
- Neglecting Detailed Planning: Failing to define the scope and objectives can lead to unstructured testing, potentially overlooking critical vulnerabilities that could be exploited.
- Ignoring Tool Updates: As cyber threats evolve, using outdated tools can leave an application exposed to new threats, undermining its security infrastructure.
- Overreliance on Automated Tools: Automated tools may miss complex vulnerabilities that manual testing could catch, compromising the thoroughness of the security assessment.
- Omitting Retesting: Without retesting, there is no confirmation that vulnerabilities are fully resolved, which may lead to persistent security threats.
Top Web Application Vulnerabilities to Watch in 2025
Here’s a list of top web application vulnerabilities that you need to identify and mitigate to strengthen their overall security posture.
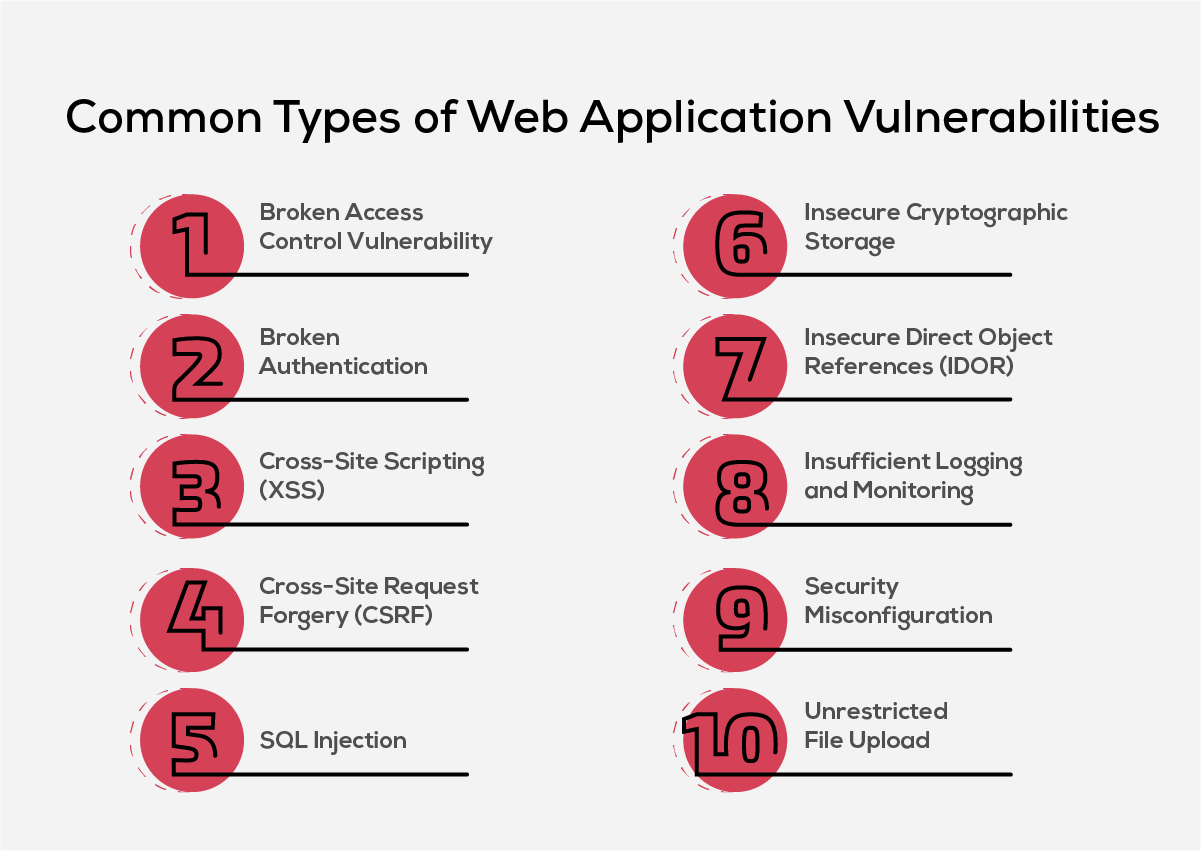
- Broken Access Control Vulnerability involves flawed access settings that let users perform tasks outside their permissions, like editing data they should only view. Attackers exploit these vulnerabilities to escalate privileges or access sensitive information, which undermines data integrity and confidentiality.
- Broken Authentication exposes systems to unauthorized access by failing to secure user identity verification. Attackers exploit weak authentication to steal credentials and impersonate legitimate users, which can lead to extensive data breaches and system compromises.
- Cross-Site Scripting (XSS) occurs when attackers inject malicious scripts into web content viewed by other users. This can hijack user sessions, deface websites, or redirect users to malicious sites, significantly compromising user interaction and data security.
- Cross-Site Request Forgery (CSRF) tricks authenticated users into executing unintended actions. Attackers exploit this to perform operations like changing passwords or transferring funds, leveraging the user’s active session without consent.
- SQL Injection lets attackers manipulate database queries through user input. They can read, modify, or delete database information, leading to unauthorized data disclosures, data loss, and in some cases, administrative access to database systems.
- Insecure Cryptographic Storage results from improperly encrypting sensitive data, making it susceptible to attacks. Issues often stem from weak algorithms or mishandled encryption keys, compromising data confidentiality and integrity.
- Insecure Direct Object References (IDOR) give attackers access to files, databases, and other resources through modifiable URL parameters. This can expose sensitive user or app data directly, bypassing normal authorization.
- Insufficient Logging and Monitoring increases vulnerability by failing to detect and respond to active security breaches promptly. Lack of detailed logging and real-time monitoring allows attackers to persist within systems undetected.
- Insufficient Session Expiration fails to log out users appropriately, allowing attackers to reuse or hijack sessions. This can lead to unauthorized access and actions, particularly in environments with sensitive operations.
- Insufficient Transport Layer Protection leaves data sent over the internet exposed to man-in-the-middle attacks. Without comprehensive TLS/SSL , sensitive information like passwords and credit card numbers can be intercepted.
- Security Misconfiguration often results from incorrect security settings or failure to secure all application layers, making applications vulnerable to various attacks due to exploitable loopholes.
- Unrestricted File Upload can lead to the server being compromised if the application fails to validate or sanitize uploaded files. This allows attackers to upload malicious files or scripts, which can be executed to gain unauthorized access or control.
- Unvalidated Redirects and Forwards can direct users to malicious sites or phishing pages. This is exploited by attackers through manipulated URLs that appear legitimate but lead to malicious destinations.
- Unvalidated Automatic Library Activation involves using outdated or insecure third-party libraries that may contain vulnerabilities. Attackers exploit these flaws to compromise applications or steal data.
- Session ID Leakage occurs when session IDs are not handled securely, allowing attackers to hijack user sessions. Poor practices such as storing session IDs in URLs or unencrypted cookies can lead to session theft, giving attackers unauthorized access to user accounts.
Each of these vulnerabilities presents a serious threat to web application security. Regular security assessments, secure coding practices, and continuous monitoring are essential to identify, fix, and prevent these issues before they are exploited.
Open-Source Security Testing Tools for Web Applications
To efficiently assess security across an organization's digital assets, penetration testers utilize a variety of sophisticated tools. These tools support different stages of web application security testing, from static and dynamic analysis to API and wireless security. Here are some of the most widely used open-source security tools:
- OWASP ZAP (Zed Attack Proxy) - A widely used, open-source DAST (Dynamic Application Security Testing) tool that helps identify vulnerabilities in web applications. It supports both automated scanning and manual testing, making it ideal for security professionals and developers.
- GitHub Code Scanning - A free, open-source static analysis tool integrated with GitHub Actions. It uses CodeQL to scan repositories for security vulnerabilities in multiple programming languages, including Java, Python, JavaScript, and C++.
- Metasploit - A powerful framework used for developing and executing exploit code against a remote target machine. It includes tools for testing security vulnerabilities, enumerating networks, and performing penetration tests.
- Arachni - A high-performance, open-source web application security scanner designed to identify vulnerabilities in modern web applications. It provides automated testing for security flaws like SQL injection, cross-site scripting (XSS), and other web-based threats.
- Akto - An open-source API security testing tool that automates API discovery and vulnerability scanning in CI/CD pipelines, ensuring secure API deployments.
- OWASP PurpleTeam - A security regression testing SaaS and CLI tool that integrates into build pipelines, allowing automated web application security testing without requiring custom test scripts.
- CI Fuzz CLI - An open-source command-line tool that enables developers to perform fuzz testing as easily as unit testing. It integrates with build systems to uncover hidden vulnerabilities early in the development lifecycle.
- Code Intelligence App - A security testing platform that integrates fuzz testing directly into CI/CD pipelines, helping developers maximize code coverage and prioritize remediation of high-impact issues.
- Contrast Community Edition (CE) - A free IAST (Interactive Application Security Testing) tool that supports Java and .NET applications. It provides real-time security analysis within applications and helps developers detect and fix vulnerabilities during runtime.
- Aircrack-ng - A powerful open-source toolset for assessing Wi-Fi security. It enables packet sniffing, WEP cracking, and WPA password brute-forcing to identify vulnerabilities in wireless networks. Pre-installed in many security-focused Linux distributions, it remains a go-to choice for wireless penetration testing.
Legal and Ethical Considerations for Penetration Testing
Penetration testing, also known as ethical hacking, is essential for detecting security weaknesses in information systems. This process involves simulated cyberattacks, which necessitates strict adherence to legal and ethical standards to ensure that such activities are conducted responsibly, safely and within defined legal boundaries.
Legal Guidelines for Penetration Testing
- Permission and Scope Definition: It's crucial to initiate penetration testing with proper authorization. Testers must secure written consent from a designated authority within the client's organization. Clearly defining what systems and networks will be tested ensures that all parties have aligned expectations and legal boundaries are respected.
- Compliance with Legal and Industry Standards: Penetration testers must stay informed about and comply with applicable cybersecurity laws and regulations. This includes understanding specific requirements of sectors like healthcare or finance, which might be governed by regulations such as HIPAA or PCI-DSS.
- Safeguarding Data Integrity: During penetration testing, protecting sensitive data is paramount. Testers should employ techniques like data anonymization and strong encryption to prevent data breaches, ensuring they adhere to data protection regulations such as GDPR and industry-specific standards.
- Defining Contractual Rights and Responsibilities: A well-defined penetration testing agreement or contract is essential. It should clearly outline the scope of testing, methodology, timelines, roles and responsibilities, liability clauses, and data handling protocols. Including confidentiality agreements ensures legal protection for both the client and the security team.
- Ethical Reporting Standards: Reporting the findings from penetration tests involves detailed documentation that should clearly communicate vulnerabilities without compromising sensitive information. Testers must manage the disclosure of these vulnerabilities responsibly to avoid exposing the client to further risks.
Ethical Guidelines for Penetration Testing
- Upholding Integrity: Ethical penetration testing demands honesty in every interaction and report. Testers should accurately represent their skills and the severity of vulnerabilities, avoiding any embellishment that could mislead clients.
- Securing Confidentiality: Maintaining the confidentiality of any information uncovered during testing is non-negotiable. Testers should use secure methods to handle and store data and should never disclose information to unauthorized parties.
- Privacy Considerations: Testers must respect privacy by minimizing the exposure of personal data during tests. This involves not only securing consent where necessary but also adhering to ethical standards that prevent unnecessary data collection.
- Maintaining Professional Competence: Penetration testers are expected to continually update their skills and knowledge to tackle emerging security threats effectively. This commitment to professional development ensures that they can offer the most current and effective security solutions.
- Managing Conflicts of Interest: Testers must disclose any potential conflicts of interest to maintain transparency with the client. Ensuring impartiality is crucial to deliver unbiased results and maintain the trustworthiness of the testing process.
These legal and ethical considerations form the backbone of responsible penetration testing practices, emphasizing the need for legality, professionalism, and respect for privacy and client data throughout the process.
Conclusion
To decisively shield your web applications from the relentless evolution of cyber threats, continuous vigilance through regular security testing is crucial. Security is not just about identifying vulnerabilities, but also about adapting quickly and staying one step ahead of cybercriminals. Integrating dynamic testing protocols, both manual and automated, ensures your defenses remain impervious. Remember, in the digital world, preemptive action isn't just advisable but imperative to safeguard your assets before attackers make their move.
Frequently Asked Questions
1. How long does web application penetration testing take?
The duration of web application penetration testing typically ranges from 1-2 weeks, depending on the complexity and scope of the assessment. In some cases, vulnerabilities may begin appearing in the testing dashboard within the first few days, allowing for early remediation. However, larger applications or those with extensive integrations may require additional time for thorough testing.
2. What are the advantages of conducting web application penetration testing?
Penetration testing provides a comprehensive security analysis that extends beyond standard vulnerability scans. It reveals hidden weaknesses in your application’s logic, infrastructure, and external APIs, helping prevent data breaches and enhancing your overall security posture.
3. What are the consequences of a web application vulnerability?
A web application vulnerability can result in significant financial losses, operational disruptions, and a severe loss of trust among users. Proactive identification and remediation of these vulnerabilities through thorough security testing and code review are critical to minimizing potential risks and safeguarding the integrity of the application.
4. Can penetration testing be performed on cloud-based web applications?
Yes, penetration testing can be conducted on cloud-hosted applications, but it requires adherence to the cloud provider’s security policies. Some providers have strict guidelines on third-party testing, and prior approval may be needed to ensure compliance with their terms of service.
5. How does penetration testing differ from vulnerability scanning?
While vulnerability scanning is an automated process that detects known security flaws, penetration testing involves a hands-on approach where security professionals actively attempt to exploit vulnerabilities. Penetration testing provides deeper insights into real-world attack scenarios, uncovering risks that automated scans may overlook.