Quick Summary: Understanding the difference between vulnerability assessments and penetration testing is key to building a strong cybersecurity foundation. This guide explores their unique roles, methodologies, and benefits, and how both contribute to a proactive defense strategy. It also covers VAPT types, testing processes, and essential policy structures. Whether you're a startup or an enterprise, discover how to apply VAPT effectively for smarter security management.
The digital world is constantly changing and protecting your business from cyber threats has become more important than ever. From securing networks and applications to meeting compliance standards, it is an undeniable pillar of modern cybersecurity strategy. Vulnerability assessment and penetration testing, often referred to as VAPT, are key components of a strong cybersecurity strategy. By regularly conducting these tests, organizations can not only mitigate potential threats but also gain a deeper understanding of their security posture, enabling informed decision-making and strategic improvements.
What is Vulnerability Assessment and Penetration Testing?
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security approach designed to uncover, assess, and address weaknesses within an organization’s IT infrastructure. It combines two distinct but complementary practices—vulnerability assessment and penetration testing—each serving a distinct purpose to provide both surface-level insights and in-depth evaluations of security posture.
While a vulnerability assessment focuses on identifying known vulnerabilities through automated scans, penetration testing takes it a step further by simulating real-world attacks to validate the actual exploitability of these flaws. Together, VAPT delivers a layered security analysis that helps organizations detect issues early, measure risk exposure accurately, and build targeted defense strategies. By integrating both these approaches, businesses can enhance their security posture and stay one step ahead of emerging threats.
Why is Vulnerability Assessment Important?
Vulnerability Assessment is a preventive process designed to identify security gaps, misconfigurations, and weak points across IT assets before they become points of entry for cyber threats. Using automated tools, it scans systems, applications, and networks against databases of known vulnerabilities to keep security teams informed of their exposure. While it does not involve actively exploiting these vulnerabilities, the insights gained are vital for ongoing patch management and compliance with industry regulations. Regular assessment help organizations maintain system hygiene, reduce attack surfaces, and build a strong baseline for security.
Why is Penetration Testing Important?
Penetration Testing is necessary for understanding how well your systems hold up under real-world attack scenarios. Unlike vulnerability assessments, which detect potential flaws, penetration testing actively attempts to exploit them—just as a malicious actor would. This controlled simulation reveals the actual impact of a breach, helping organizations evaluate the effectiveness of their existing defenses. It plays a key role in testing the strength of security controls, uncovering complex vulnerabilities that may evade automated scans, and offering practical insights for risk prioritization. By simulating the approach of a real attacker, penetration testing uncovers how deeply systems can be compromised—and underscores the urgency of closing critical gaps.
Types of Vulnerability Assessments
Different systems require different levels of scrutiny—this is why organizations rely on various types of vulnerability assessments to secure their IT environments. Each assessment focuses on a specific area of the infrastructure, helping ensure well-rounded protection against evolving cyber threats. Here’s a look at the most widely used types:
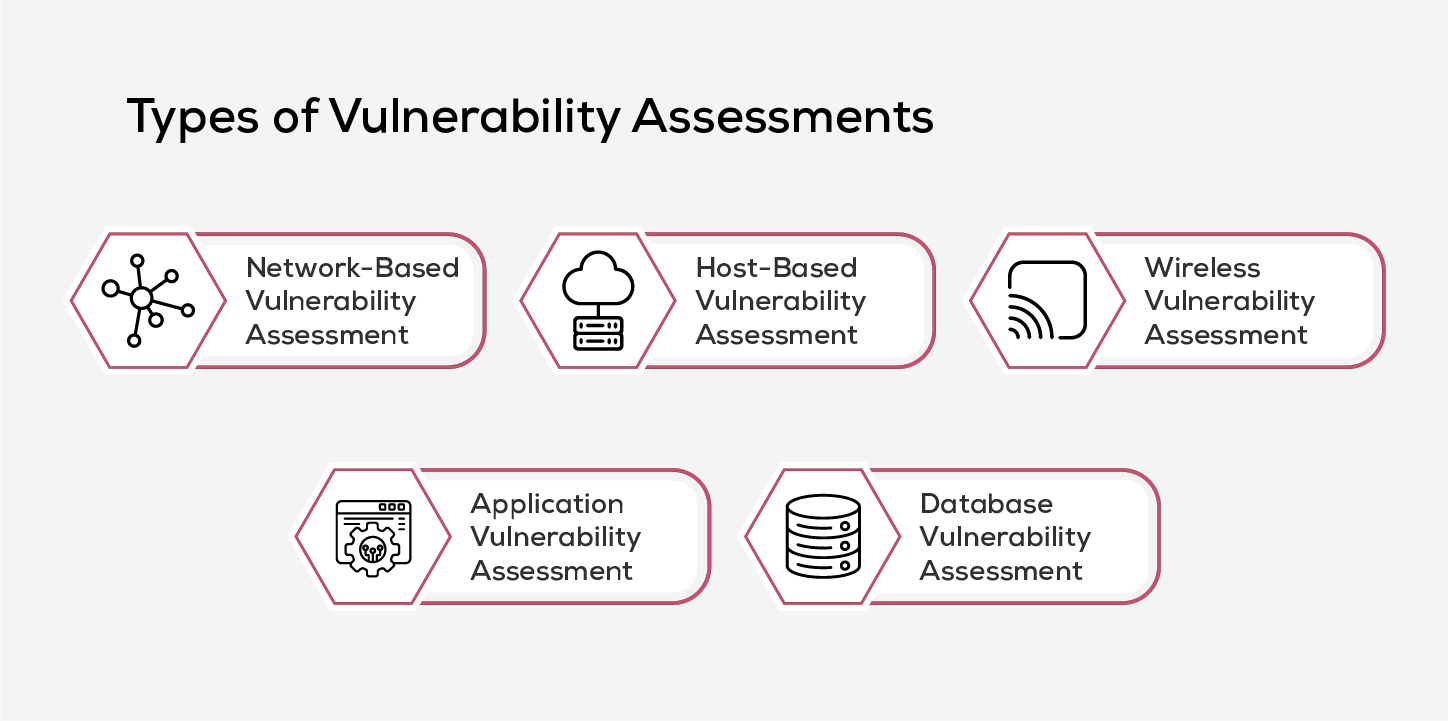
1. Network-Based Vulnerability Assessment
This assessment identifies exposed systems within both wired and wireless networks. It helps detects vulnerabilities such as open ports, unauthorized devices, or misconfigured firewalls that could serve as potential entry points for attackers.
2. Host-Based Vulnerability Assessment
This type of assessment focuses on individual systems such as critical servers, endpoints, and workstations. It evaluates operating systems, software and configurations to detect vulnerabilities, patch gaps and local security issues. The scan offers detailed insights into registry settings, and local exposures on each host machine.
3. Wireless Vulnerability Assessment
Designed to analyze an organization’s wireless landscape, this assessment identifies rogue access points, insecure configurations, and unauthorized devices. It helps secure Wi-Fi networks by validating encryption standards and access controls, and ensuring proper network segmentation.
4. Application Vulnerability Assessment
Primarily used for web and software applications, this assessment inspects for known coding vulnerabilities, insecure APIs, misconfigurations, and outdated components that could be exploited by external attackers or internal users, helping organizations fortify their application threats.
5. Database Vulnerability Assessment
This assessment identifies security risks within databases and big data environments, including weak permissions, misconfigurations, exposed credentials, and unpatched flaws. It helps secure critical data storage from internal misuse and external threats.
Each of these assessments serves a specific purpose and collectively contributes to a comprehensive vulnerability management strategy. Regularly performing the right type—or a combination of them can significantly reduce the organization’s attack surface.
Types of Penetration Testing
Penetration testing isn't one-size-fits-all. Different testing types target different attack surfaces, and each is chosen based on specific business objectives and risk areas.
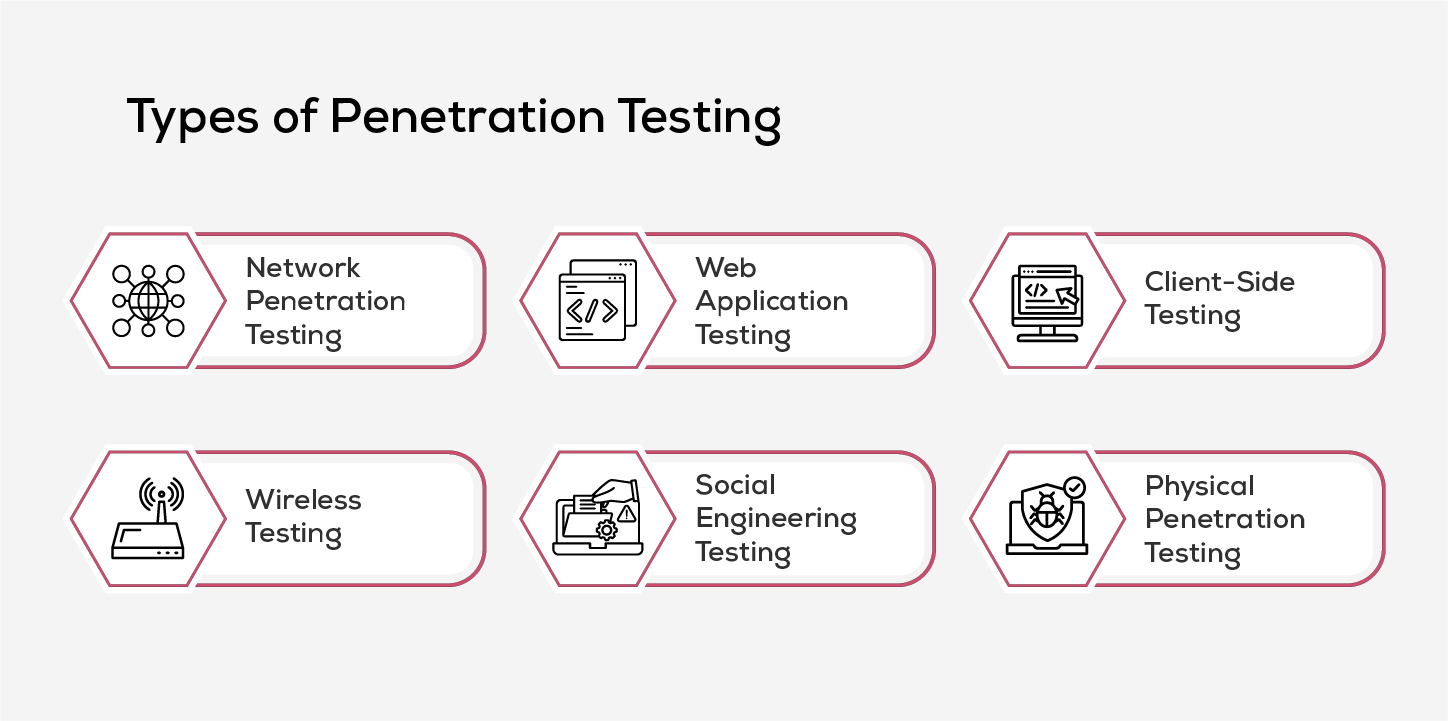
1. Network Penetration Testing
This type of testing helps uncover vulnerabilities within the network infrastructure, including servers, firewalls, endpoints and routers. By simulating attacks like MITM and DNS exploits, it helps prevent real-world exploitation of security gaps.
2. Web Application Testing
Aimed at exposing flaws in online platforms, web app testing ensures issues in code, APIs, and configurations are found and mitigated early. This form of testing is detailed and complex, requiring thorough planning and assessment of all endpoints that users interact with. The objective is to uncover vulnerabilities in the application's code, database, and backend systems that could be exploited.
3. Client-Side Testing
Focusing on applications running on end-user machines, client-side penetration testing uncovers vulnerabilities in commonly used software like web browsers, email clients, and office tools. By simulating real-world attack scenarios it helps detect weak points that could compromise user systems from within.
4. Wireless Testing
It involves assessing the security of wireless networks by identifying and evaluating the connections between devices linked to the business’s Wi-Fi. This includes devices like laptops, smartphones, and tablets, gadgets and these tests are generally conducted onsite to ensure the pen tester is within range of the network’s signal.
5. Social Engineering Penetration Testing
Social engineering penetration testing evaluates how easily employees can be manipulated into revealing sensitive information. Instead of targeting systems, it tests human behavior through simulated attacks like phishing, vishing, smishing, tailgating, and impersonation. This helps identify gaps in security awareness and strengthens defenses against real-world threats.
6. Physical Penetration Testing
Physical penetration testing simulates real-life break-in attempts to uncover flaws in an organization’s physical security—like weak locks, poor surveillance, or unmonitored entry points—helping strengthen defenses against unauthorized access.
Read more about Penetration Testing to protect your organization from emerging cyber threats.
Popular Tools for VAPT
A successful vulnerability assessment and penetration testing (VAPT) strategy depends not only on methodology but also on the right tools. These tools enhance accuracy, speed, and depth of testing across various systems and applications.
- Nessus – Performs in-depth vulnerability scanning across systems, networks, and applications.
- Metasploit – A powerful framework for simulating real-world attacks during penetration testing.
- Burp Suite – Focuses on identifying security flaws in web applications.
- OWASP ZAP – A widely-used open-source tool for scanning web vulnerabilities.
Explore our detailed guide on VAPT Tools to learn how each tool supports different stages of the security testing lifecycle.
Key Steps in Vulnerability Assessment
Conducting a vulnerability assessment involves more than just scanning systems for flaws—it’s a structured, repeatable process that helps organizations stay resilient against emerging threats. To ensure maximum value, the assessment must be integrated into an ongoing security program, ideally supported by a DevSecOps approach where development, security, and operations teams collaborate seamlessly.
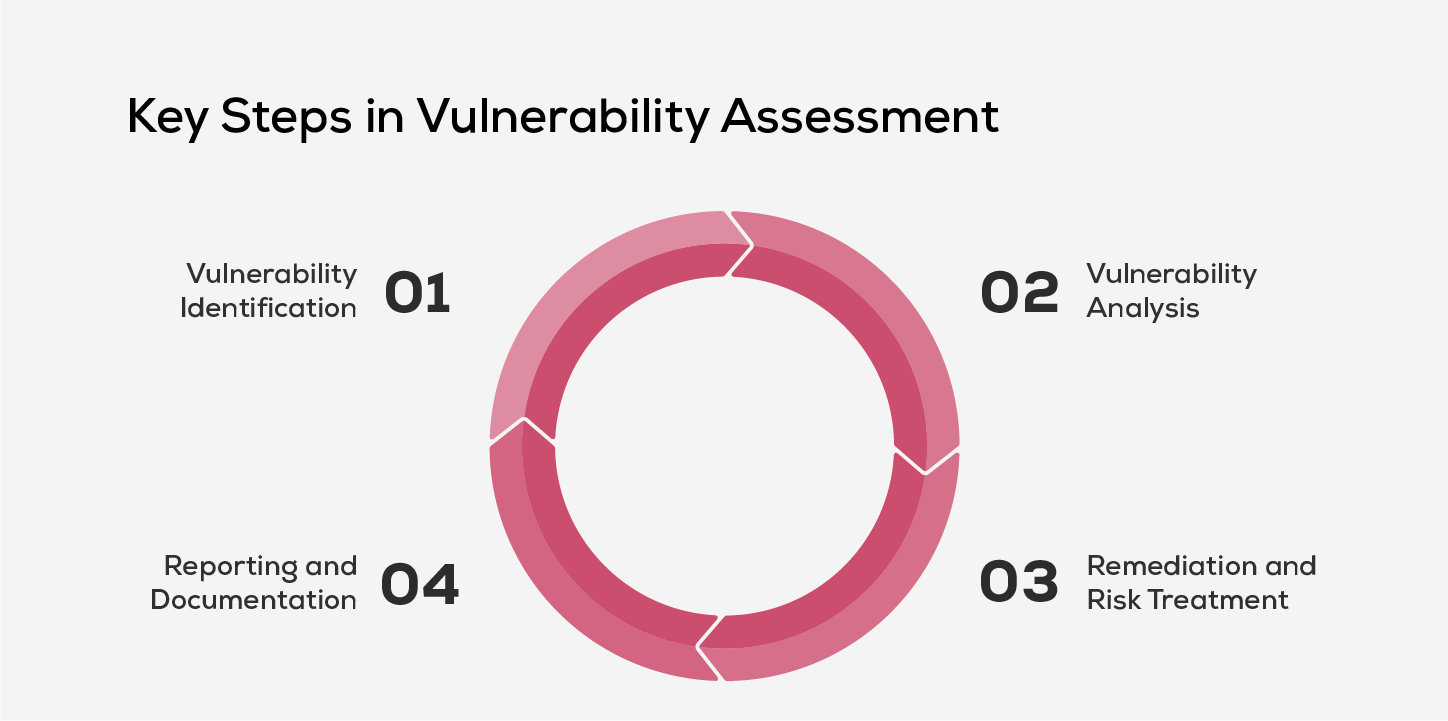
Here’s a breakdown of the key stages in the vulnerability assessment process:
1. Vulnerability Identification
This foundational step involves creating a comprehensive inventory of vulnerabilities across systems, servers, applications, and devices. Organizations use automated vulnerability scanning tools, manual testing, threat intelligence feeds, vendor advisories, and asset inventories to detect potential weaknesses. This stage also helps define the organization’s risk tolerance, potential business impact, existing countermeasures, and the scope of acceptable residual risk.
2. Vulnerability Analysis
Once vulnerabilities are identified, the next step is to determine their root cause. This involves analyzing system components to trace the origin of the vulnerability—whether it’s due to misconfigurations, outdated software, or flawed design. Understanding the source allows teams to apply targeted fixes rather than generic workarounds.
3. Remediation and Risk Treatment
In this stage, organizations prioritize and address the identified vulnerabilities. The DevSecOps team typically collaborates to decide the best course of action—be it applying patches, updating configurations, or introducing new controls. The remediation process may also involve operational changes or deploying tools to close any security gaps.
4. Reporting and Documentation
The final step involves generating a detailed vulnerability assessment report, which acts as a reference for ongoing improvements and compliance audits. It typically includes the vulnerability name, discovery date, CVE score, affected systems, potential impact, mitigation steps, and where applicable, a proof of concept. Clear documentation ensures transparency and guides future assessments.
A vulnerability assessment is an ongoing effort that evolves with the evolving threat landscape. When embedded into regular workflows and supported by cross-functional teams, it becomes a powerful tool for strengthening cybersecurity and improving risk management over time.
Key Steps in Penetration Testing
Penetration testing is a structured and goal-oriented process designed to mimic the actions of real-world attackers. By progressing through clearly defined stages, ethical hackers can uncover critical vulnerabilities, assess their exploitability, and provide actionable insights to strengthen security controls.
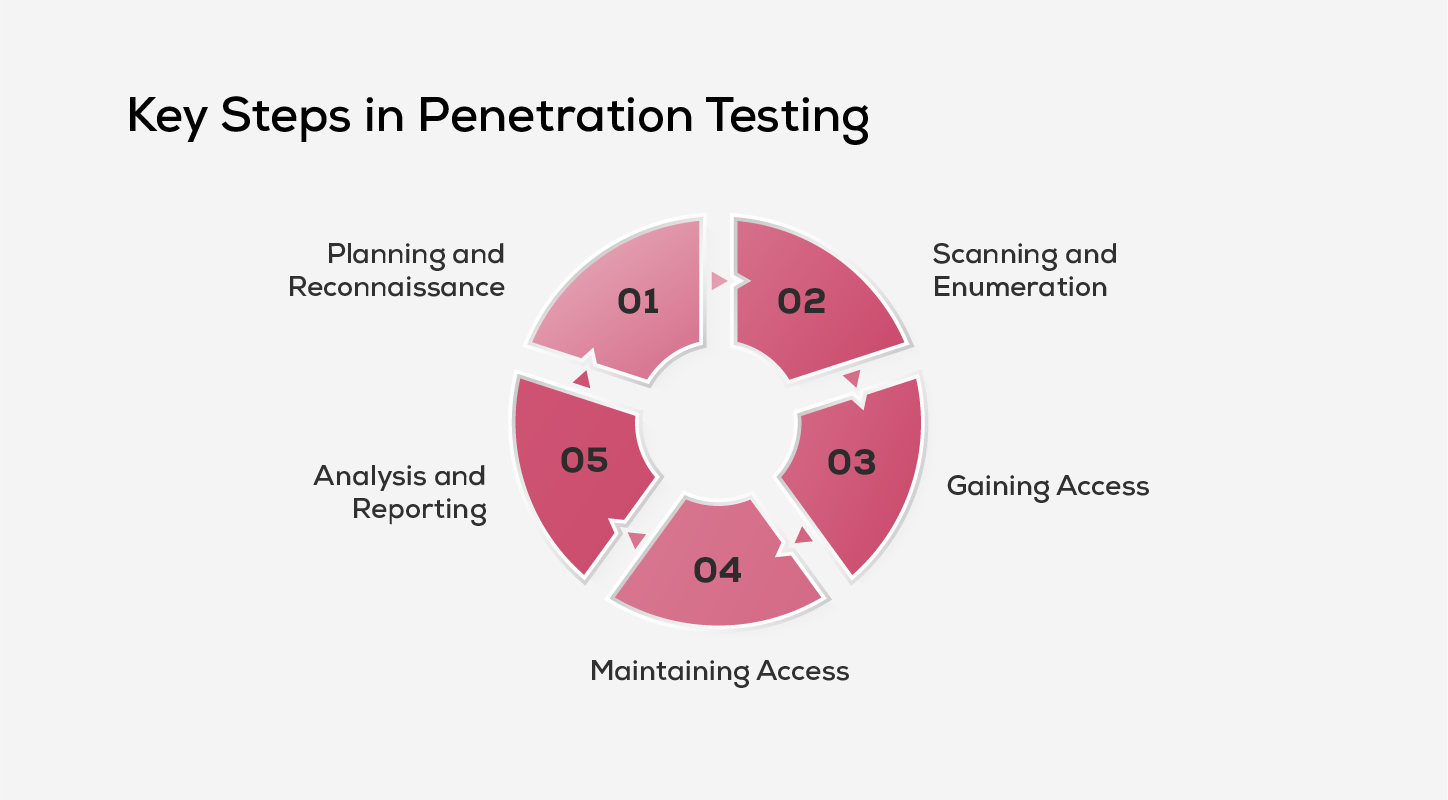
Here’s a breakdown of the five core stages in a typical penetration test:
1. Planning and Reconnaissance
This initial phase sets the direction for the entire test. It involves:
- Scope Definition: Establishing the boundaries of the test— specifying which systems will be tested, which methods are permitted, and what success criteria will be used.
- Information Gathering: Collecting publicly available data such as domain names, IP ranges, mail servers, and employee directories to map out potential attack surfaces.
The more thorough the reconnaissance, the more targeted and effective the test will be.
2. Scanning and Enumeration
At this stage, testers analyze how the target system responds to various intrusion attempts. Two main scanning methods are used:
- Static Analysis: Reviewing source code or binaries without executing the application to identify potential flaws.
- Dynamic Analysis: Observing the application in its runtime environment to detect vulnerabilities in real-time, such as improper input validation or memory leaks.
This step helps identify exploitable weaknesses and entry points.
3. Gaining Access
After mapping the attack surface and identifying vulnerabilities, ethical hackers attempt to exploit them using techniques such as:
- SQL injection
- Cross-site scripting (XSS)
- Command injection
- Credential brute-forcing
The goal is to breach the system, escalate privileges, extract sensitive data, or hijack user sessions to evaluate the potential business impact.
4. Maintaining Access
In this stage, testers simulate the behavior of advanced persistent threats (APTs) by attempting to establish a long-term presence within the system—typically through backdoors or compromised accounts. The goal is to assess how long an attacker could remain undetected and the depth of their potential infiltration.
Understanding persistence is crucial for evaluating response readiness and improving detection mechanisms.
5. Analysis and Reporting
The final stage involves compiling all findings into a detailed penetration testing report. It typically includes:
- Vulnerabilities exploited
- Data accessed or manipulated
- Attack paths and privilege escalation techniques
- Duration of undetected presence
- Recommendations for remediation
This report becomes a roadmap for the security team to fine-tune firewalls, patch systems, and improve overall security posture.
When executed systematically, these penetration testing stages provide organizations with a practical, risk-based view of their defences—bridging the gap between theoretical security and real-world resilience.
What is the Difference Between Vulnerability Assessment and Penetration Testing?
Vulnerability Assessment and Penetration Testing are often mentioned together, but they serve distinct purposes within an organization’s security strategy. While both are essential for identifying and addressing risks, their methods, depth, and outcomes vary significantly. Let’s look at how they differ from each other.
1. Faster Insights with Automation
Vulnerability Assessment is typically faster, using automated scanners to inspect systems, networks, and applications for known flaws. Reports can be generated within minutes to a few hours, depending on the scale and configuration. These frequent scans help teams maintain continuous visibility into their security posture.
Penetration Testing involves manual exploration by cybersecurity experts, replicating the behavior of real-world attacks. Due to its hands-on nature, it takes significantly longer—often up to two to three weeks—to complete a thorough test.
Vulnerability Assessment offers quicker execution, making it ideal for routine checks.
2. Thorough Evaluation of Real-World Threats
Vulnerability Assessment offers a broad overview, identifying known vulnerabilities such as outdated software, weak configurations, or unpatched systems. However, it may miss context-specific flaws or produce false positives without assessing real exploitability.
Penetration Testing delivers deeper insights by attempting to exploit detected vulnerabilities. It uncovers hidden threats, business logic errors, and chained attack scenarios that automated tools might overlook.
Penetration Testing provides a more detailed and realistic evaluation.
3. Risk Analysis that Goes Beyond Numbers
Vulnerability Assessment classifies vulnerabilities based on severity scores like CVSS, enabling teams to prioritize issues based on how widespread or easy to exploit they are in general scenarios.
Penetration Testing brings in context—evaluating how a vulnerability behaves in the organization’s specific environment. It offers a more practical understanding of risk by validating whether theoretical threats translate into actual breaches.
Penetration Testing delivers contextual, real-world risk insights.
4. Reports that Drive Action and Strategy
Vulnerability Assessment generates detailed, structured reports listing all discovered vulnerabilities, their descriptions, affected assets, and recommended patches. These are ideal for maintaining compliance and guiding standard remediation workflows.
Penetration Testing reports are more comprehensive. They include real-world attack scenarios, proof-of-concept evidence, attack paths, and business impact assessments. These reports are often used strategically to enhance incident response and overall defense strategies.
Penetration Testing offers richer, more actionable reporting.
5. Support for Evolving Compliance Needs
Vulnerability assessments are crucial for helping organizations meet regulatory requirements. By maintaining documented evidence of routine scans and timely resolutions, businesses can demonstrate due diligence in adhering to compliance standards like PCI DSS, HIPAA, and ISO 27001.
Penetration testing complements this by validating the effectiveness of implemented controls through real-world attack simulations. Many standards mandate annual penetration tests to ensure that existing defenses can withstand evolving threats.
A balanced combination, depending on compliance scope and frequency.
6. Guided Fixes with Tactical Clarity
Vulnerability assessment reports typically highlight known flaws and link to existing solutions—such as patches or upgrade instructions. However, the remediation process may require further interpretation or expert consultation for proper execution.
Penetration testing with its manual and targeted approach, offers richer remediation details. These reports often include proof-of-concept exploits, specific misconfiguration fixes, and system-hardening recommendations tailored to the environment tested.
Penetration Testing excels in offering depth and clarity for remediation support.
7. Flexible Options to Match Your Budget
Vulnerability assessments are more cost-efficient, driven by automation and scalability. Depending on the organization’s size and frequency of scans, they typically range from $1,000 to $4,500 per year.
Penetration testing involves manual expertise, planning, and environment-specific exploration. This added depth comes at a premium, with prices ranging from $5,000 to over $70,000 based on complexity, scope, and the tester’s experience.
Vulnerability Assessment offers affordability and ideal for routine use.
8. Tailored Fit for Diverse Security Goals
Vulnerability assessments are ideal for startups, SMEs, and organizations with agile deployment cycles or resource constraints. They offer continuous security visibility at manageable costs.
Penetration testing is more suited for enterprises in high-security domains like finance, healthcare, or critical infrastructure—where precision, depth, and tailored insights are crucial for safeguarding sensitive systems.
Penetration Testing is ideal for enterprises with advanced security needs.
Building the Right Security Policies
Strong cybersecurity isn’t just about tools and testing—it’s also about having the right policies in place. These policies promote consistency, accountability, and alignment across teams, making your vulnerability assessment and penetration testing (VAPT) efforts more effective. Two key policy documents support this: the Vulnerability Assessment Policy and the Penetration Testing Policy.
Vulnerability Assessment Policy
This policy serves as a structured guideline for carrying out routine scans to identify weaknesses across systems and applications. It ensures a consistent approach to discovering and managing vulnerabilities, even in fast-paced IT environments.
- Purpose: To establish standardized procedures for detecting known vulnerabilities using automated tools.
- Scope: Define which networks, endpoints, or assets fall under the scanning cycle.
- Frequency: Typically conducted weekly, monthly, or post-deployment, based on business risk level.
- Reporting and Remediation: Details how findings are reported, prioritized, and addressed through patching or system updates.
- Compliance Support: Reinforces continuous monitoring and audit preparedness for various industry regulations.
Penetration Testing Policy
To simulate real-world cyber threats effectively, organizations need more than just tools—they need structure. A well-defined Penetration Testing Policy ensures that ethical hacking activities are conducted safely, systematically, and with minimal disruption to business operations.
- Purpose: To assess how well existing security controls hold up against simulated cyberattacks.
- Scope: Identifies the specific systems, applications, or environments to be tested.
- Frequency: Often scheduled annually, bi-annually, or after major infrastructure changes.
- Reporting and Remediation: Includes documentation of attack techniques used, exploited paths, and remediation strategies tailored to the organization.
- Compliance Support: Helps fulfill mandatory testing requirements under standards like PCI DSS, HIPAA, and ISO 27001.
These policies form the backbone of a disciplined security framework, helping organizations ensure consistency, accountability, and continuous improvement in their VAPT efforts.
What Makes Inspirisys VAPT a Trusted Solution?
- Defined Scope: Aligned to your business goals and infrastructure.
- Deep Intelligence Gathering: Domains, IPs, services—mapped with precision.
- Smart Vulnerability Detection: Pinpoints vulnerabilities with advanced scanning tools.
- Risk-Based Planning: Prioritized strategies for focused testing and business relevence.
- Real-World Exploits: Simulates actual attack paths and privilege escalation.
- Impact Analysis: Assesses exploit outcomes for better decisions.
- Clear Reporting: Actionable insights with remediation guidance.
- Post-Test Cleanup: Ensures systems are restored and key learnings are applied to prevent future issues.
Inspirisys VAPT services are designed to align with your CI/CD workflows, meet regulatory needs, and support business priorities—helping you stay secure, informed, and ahead.
Conclusion
Every organization has its own security maturity level, risk tolerance, and operational constraints. Choosing between vulnerability assessment and penetration testing—or adopting both—boils down to the level of insight required versus the resources available. While vulnerability assessments offer fast, ongoing visibility, penetration testing provides deeper, real-world threat validation.
For a well-rounded and effective cybersecurity strategy, consider adopting a comprehensive VAPT approach like Inspirisys'. This combined methodology empowers you to make informed decisions about where to prioritize security resources and ultimately strengthens your overall defensive posture.
Frequently Asked Questions
1. What are the main categories of vulnerability assessments?
While there are several types, the vulnerability assessments typically fall into three core categories namely, web vulnerability assessments, application assessments and network assessments. Each targets specific layers of your IT environment to uncover potential weaknesses.
2. Who is a penetration and vulnerability tester?
A penetration and vulnerability tester is a cybersecurity professional who identifies and assesses weaknesses in systems. A vulnerability tester scans and evaluates systems to find known security flaws, while a penetration tester (or ethical hacker) goes a step further by simulating real-world cyberattacks to exploit these weaknesses and test how deep an attacker could go. Together, these roles help organizations proactively strengthen their security.
3. Are vulnerability assessments the same as penetration testing?
Not quite. A vulnerability assessment scans known weaknesses and provides a risk overview using automated tools, while penetration testing goes a step further by actively exploiting those weaknesses to demonstrate the real-world impact of a potential breach.
4. How is penetration testing different from ethical hacking?
Penetration testing is a focused exercise that simulates attacks within a defined scope to find exploitable flaws. Ethical hacking is broader—it includes pen testing but also involves evaluating security policies, identifying risks, and recommending defensive strategies.
5. What are red, blue, and purple teams—and how do they relate to VAPT?
Red, blue, and purple teams represent offensive, defensive, and collaborative roles in cybersecurity. Red teams simulate attacks like penetration testers, blue teams on the other hand respond and strengthen defenses, much like post-assessment remediation in VAPT. Purple teams combine both to enhance the overall effectiveness of VAPT initiatives.